i3indya™ Technologies presents Practical Training on Ethical Hacking & Cyber Security via VIDEO LECTURE's.
If you want to know how hackers are attacking your websites, emails, servers & computer remotely or how you can protect yourself or your organization from all these attacks then this is the right course for you.
Ethical Hacking (Video Lectures)
45 Hrs
INR 6999/-
Certificate of Completion by i3indya™ Technologies
20 Topics | Learn 100+ Secrets of Ethical Hacking
 Yes! You can Do This Course at Your Home by purchasing our distance learning kit. Click Here
Yes! You can Do This Course at Your Home by purchasing our distance learning kit. Click Here
| Module | Topics | Duration (HH:MM:SS) |
|---|---|---|
|
1 |
Introduction |
|
|
1.1 |
|
00:06:00 |
|
1.2 |
Types of Hackers |
00:05:00 |
|
1.3 |
Phases of Hacking |
00:09:00 |
|
1.4 |
Career Opportunities |
00:05:00 |
|
2 |
Creating Your Virtual Lab |
|
|
2.1 |
Installing Kali & Metasploitable |
00:11:00 |
|
2.2 |
Linux Basics |
00:14:00 |
|
2.3 |
Linux File Permissions |
00:05:00 |
|
3 |
Networking |
|
|
3.1 |
|
00:13:00 |
|
3.2 |
IPv6 |
00:07:00 |
|
3.3 |
NAT (Network Address Translation) |
00:02:00 |
|
3.4 |
OSI Layer |
00:14:00 |
|
3.5 |
Other Networking Terms & Devices |
00:07:00 |
|
4 |
Information Gathering & Scanning |
|
|
4.1 |
Information Gathering (Part-1) |
00:05:00 |
|
4.2 |
Information Gathering (Part-2) |
00:08:00 |
|
4.3 |
Information Gathering (Part-3) |
00:04:00 |
|
4.4 |
Information Gathering (Part-4) |
00:04:00 |
|
4.5 |
Scanning |
00:10:00 |
|
5 |
Google Hacking |
|
|
5.1 |
Understanding Google Hacking |
00:07:00 |
|
5.2 |
Google Dorks |
00:13:00 |
|
6 |
Metasploit Framework |
|
|
6.1 |
Introduction to Metasploit Framework |
00:06:00 |
|
6.2 |
System Hacking (WIndows XP) |
00:09:00 |
|
6.3 |
Hacking Linux with Metasploit |
00:06:00 |
|
6.4 |
introduction to Armitage |
00:05:00 |
|
7 |
Malwares |
|
|
7.1 |
Malwares (Part-1) |
00:06:00 |
|
7.2 |
Malwares (Part-2) |
00:05:00 |
|
8 |
WiFi Hacking |
|
|
8.1 |
Wi-Fi Terms (Part-1) |
00:05:00 |
|
8.2 |
Wi-Fi Terms (Part 2) |
00:00:00 |
|
8.3 |
Understanding 802.11x |
00:08:00 |
|
8.4 |
WPA2 Cracking |
00:12:00 |
|
9 |
Web App Security |
|
|
9.1 |
Introduction to Web Applications |
00:10:00 |
|
9.2 |
|
00:16:00 |
|
9.3 |
Arbitrary Code Execution |
00:08:00 |
|
9.4 |
CSRF |
00:07:00 |
|
9.5 |
SQL Injection |
00:10:00 |
|
9.6 |
XSS |
00:15:00 |
|
9.7 |
Shell Exploits |
00:06:00 |
|
10 |
Denial of Service |
|
|
10.1 |
Introduction to DoS |
00:02:00 |
|
10.2 |
Types of DoS attack |
00:09:00 |
|
10.3 |
Introduction to DDoS |
00:08:00 |
|
10.4 |
Prevention of DoS Attacks |
00:06:00 |
|
11 |
Cryptography |
|
|
11.1 |
Introduction to Cryptography |
00:08:00 |
|
11.2 |
Basic Cryptography Techniques |
00:09:00 |
|
11.3 |
CryptoSystem |
00:08:00 |
|
11.4 |
Various Type of Encryption |
00:12:00 |
|
11.5 |
Enigma and other Cryptography Service |
00:06:00 |
|
12 |
Firewall,IDS &IPS |
|
|
12.1 |
Firewall |
00:09:00 |
|
12.2 |
Various types of Firewalls (Part-1) |
00:08:00 |
|
12.3 |
Various types of Firewalls (Part-2) |
00:11:00 |
|
12.4 |
IDS |
00:08:00 |
|
12.5 |
IPS |
00:04:00 |
|
13 |
Final Exam |
|
|
13.1 |
Ethical Hacking Exam |
00:30:00 |
Latest and Updated Topics are covered
We concentrate not only on Hacking but also on Security of all Topics
Forensics on almost all platforms and devices are taught
Hands on training with live demonstrations
Well experienced Trainers
Tied up with several Government Organizations for Training and Consultancy
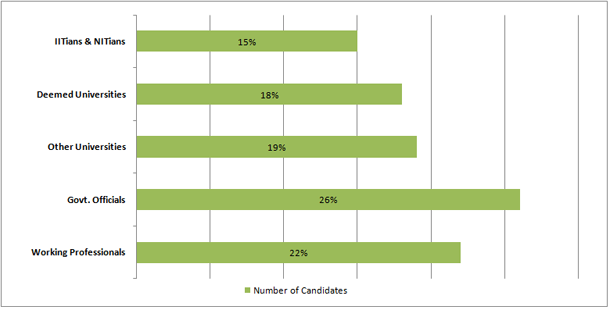
Trained more than 30,000 professionals from all over India
Providing training to CBI, NIA and State Police across India
We limit our tool usage from third-party and we provide manual approach for each Technique
We also design our own tools
Basics of Computer
Knowledge of how to use internet
Basics of Networking
College students seeking career in Cyber Security Industry.
Person having interest in Hacking & Security.
Education Faculty & Staff.
IT Professionals, Web Developers, Network Engineers.
Students from any branch can join the training.