i3indya™ Technologies presents Summer Training on "i3indya Ethical Hacking & Cyber Security - iEHCS (30 Days)".
The rapid and dramatic advances in information technology (IT) in recent years have without question generated tremendous benefits. However, they have created significant and unprecedented risks to operations. Computer security has, in turn, become much more important as all levels of an organization to utilize information systems security measures to avoid data tampering, fraud, disruptions in critical operations, and inappropriate of sensitive information.
After the boom in Networking and Software jobs, the past two year have seen a sharp rise in the field of information security. Information Security and Ethical Hacking is the latest buzzword in the industry. In the past five years, the percentage of hacking crimes, data thefts, data losses, viruses and other cyber crimes have increased exponentially.
Course Highlights
| Course | : | i3indya Ethical Hacking & Cyber Security (iEHCS) |
| Certification | : | Participation Certificate by i3indya™ Technologies |
| Study Material | : | Books & CD Free to each participant |
| Topics | : | 12 Live Cyber Cases, 10 Case Studies, 3 Hacking Projects will be covered |
Fees & Duration
| Module | Duration | Fee |
|---|---|---|
| Advance Module 1.1 | 45 Hrs/15 Days | 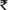 5,700/- (including taxes) per candidate 5,700/- (including taxes) per candidate |
| Advance Module 1.1+1.2 | 90 Hrs/30 Days | 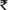 11,628/- (including taxes) per candidate 11,628/- (including taxes) per candidate |
| Advance Module 1.1+1.2+2.0 | 120 Hrs/40 Days |  16,188/- (including taxes) per candidate 16,188/- (including taxes) per candidate |
special Discount Offer
Submit your fee on or before 1st June, 2016 and get discount of  900 on iEHCS Advance Module 1.1+1.2
900 on iEHCS Advance Module 1.1+1.2
» Total fee to submit after discount is  10,649/-
10,649/-
Want TO DO THIS COURSE for FREE ?
Here is the Opportunity to Join this course for FREE, Try Your Luck Here !
Do This Course At Your Home
Yes! You can do this course at your home by purchasing our distance learning kit. See details Here
Training Modules
|
DAY |
TOPICS |
|
1 |
Fundamental of Ethical Hacking |
|
2 |
Overview of Cyber Law |
|
3 |
Information Gathering |
|
4 |
Virtualization & System Cloning |
|
5 |
Windows Hacking & Security (Win 8 & Win 7) |
|
6 |
Password Cracking Techniques |
|
7 |
Data Hiding Techniques |
|
8 |
Hacking By Batch Programming & Scripting |
|
9 |
Hacking by Viruses, Trojans, Keyloggers & Spywares |
|
10 |
Malware Analysis & Fake Antivirus Detections |
|
11 |
IDS, IPS and Honeypots |
|
12 |
Proxy Server & Virtual Private Network (VPN) Technology |
|
13 |
Google Database Hacking |
|
DAY |
TOPICS |
|
14 |
Email Hacking & Security Issues |
|
15 |
Facebook Hacking, Security & Forensic |
|
16 |
Clickjacking & Tabnabbing Attacks |
|
17 |
Advanced Methodology for Privacy on Internet |
|
18 |
Social Engineering |
|
19 |
Android Hacking, Security & Forensics |
|
20 |
Credit Card Frauds & Cases |
|
21 |
Website & Database Hacking Attacks |
|
22 |
Web Server Hacking & Security |
|
23 |
Vulnerability Assessment & Penetration Testing Tools & Methodologies |
|
24 |
Wireless Hacking & Countermeasures |
|
Exam – Theory & Practical |
|
DAY |
TOPICS |
|
25 |
Linux Hacking & Security |
|
26 |
Macintosh Hacking & Forensic |
|
27 |
Switch & Router Devices Hacking |
|
28 |
Network Security & Hacking |
|
29 |
Cyber Forensics Investigations & Evidence Recovery |
|
30 |
Audio, Video & Image Forensics |
|
31 |
Cyber Crime Investigation |
|
32 |
Case Study ( Live Demo By i3indya Team ) |
|
Exam – Theory & Practical |
WHY iEHCS ?
» 12 Live Cyber Cases, 10 Case Studies, 3 Hacking Projects will be covered
» Latest and Updated Topics are covered
» New Topics like Hacking & Securing Linux, Android, Mac, Web Servers are taught
» We concentrate not only on Hacking but also on Security of all Topics
» Forensics on almost all platforms and devices are taught
» Hands on training with live demonstrations
» Well experienced Trainers
» Tied up with several Government Organizations for Training and Consultancy
» Trained more than 30,000 professionals from all over India
» Providing training to CBI, NIA and State Police across India
» We limit our tool usage from third-party and we provide manual approach for each Technique
» We also design our own tools
Pre Requisite
» Basics of Computer
» Knowledge of how to use internet
» Basics of Networking
Recommendation
It is strongly recommended to bring your own LAPTOP during the training so that you can easily practice the exercises at home.
Who Could Attend ?
» College students seeking career in Cyber Security Industry.
» Person having interest in Hacking & Security.
» Education Faculty & Staff.
» IT Professionals, Web Developers, Network Engineers.
» Students from any branch can join the training.
Program Benefits & Highlights
» Learn & Interact with renowned Industry Experts.
» Receive an unparalleled education on the art of computer security with personal one-on-one attention.
» Hands on Demonstrations of Latest Hacking Techniques & Tools.
» Hands on Demonstrations of various cases solved by our trainer.
» Power Point Presentation, Live Demos, Interactive Question & Answer sessions and comprehensive
reading material.
» FREE - Book & CD Free to each participant
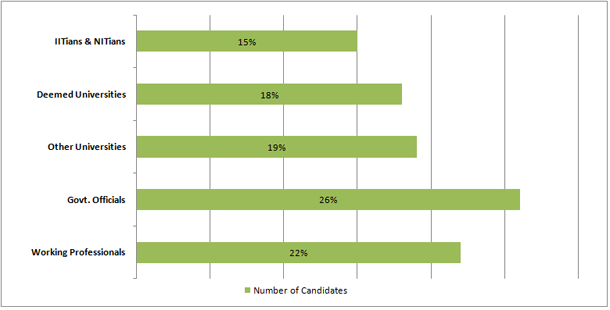
WHO ATTENDED iEHCS ?
Training Centers
Delhii3indya Technologies |
Batch Details
| Date | Timing Schedule | |
| 16-May-2016 | 09:20 am - 12:20 pm | |
| 25-May-2016 | 12:40 pm - 03:40 pm | |
| 07-Jun-2016 | 03:50 pm - 06:50 pm | |
| 13-Jun-2016 | 09:20 am - 12:20 pm | |
| 22-Jun-2016 | 12:40 pm - 03:40 pm | |
| 11-Jul-2016 | 03:50 pm - 06:50 pm |
Registration Procedure
To complete your Registration for i3indya Summer Training program, kindly follow the following steps:
» Step 1 : Register yourself online for Summer Training. Click Here
After you register online, you will get a confirmation mail of your registration along with your Token Number.
» Step 2 : Download the Training Registration Form here ![]()
» Step 3 : Pay Training Fee (See Modes of Payment Below)
» Step 4 : Send us following documents :
1) 1 ID proof copy (Driving License/Voter ID Card)
2) Training Registration Form (completely filled & signed)
3) Fee Payment Receipt (transaction screenshot/cash deposit receipt)
to the following address:
i3indya Technologies
G 85, Preet Vihar, Vikas Marg, New Delhi - 110092
Contact: +91 - 95 6060 5666 (Ext: 2)
or mail the above documents at training@i3indya.com
Note : Your Seat will be confirmed only once we receive your Training Registration Form and Fees. You will get a e-Receipt as a confirmation of your registration.
Modes of Payment
» Mode 1 - Via Net-banking (NEFT or IMPS) : Transfer the amount directly to following bank account no. via IMPS/NEFT. Keep screenshot of transaction successful page as payment receipt.
» Mode 2 - Cash Deposit in Bank A/C : Submit your fees via Cash into Company's Bank Account and keep copy of cash deposit receipt as payment receipt.
Bank account details are as follows:
 Open Yes Bank Branch List |
|
| Bank Name | YES BANK LTD |
| Account Name | I THREE INFOTECH PVT.LTD. |
| Account Number | 023683900000560 |
| Branch Name | Preet Vihar New Delhi |
| IFSC Code | YESB0000236 |
| Zone | Preet Vihar New Delhi |
» Mode 3 - Submit your cash at Our Training Center
» Mode 4 - Pay Instantly with Credit Card/ Debit Card/ Net Banking from any of the following gateway:
For More Information
Contact : +91 - 95 6060 5666 (Extenstion 2)
Or Fill Quick Enquery Form below
-
Talk to Expert
 For more details call at
For more details call at
+91 - 95 6060 5666
(Extension : 2)
Timings : 10am - 8pm -
i3indya Govt. Clients
-
The Best Training Provider

-
COLLEGES COVERED
-
SUBSCRIBE FOR UPDATES
Study Material